Let’s face it, you are reading this article in order to Configure Cisco ASA 5506-X for PPPoE Passthrough because you may need to replace your standard ISP router. Although ISP Routers do a good job, there is always the need to use a dedicated device which suits your requirements. Unlike some popular routers on the Market, the Cisco ASA 5506 as well as the older ASA 5505 do not have support for ADSL.
Other popular routers like the 887va and 1914 come with SHDSL modules to cater for your PPPoE needs but it is not the case for the most loved Cisco ASA Security Devices. Cisco always cater for the business requirement at hand and so has provisioned a way to configure a PPPoE passthrough for your network in order to terminate connectivity to the trusted network device.
Configure Cisco ASA 5506-X for PPPoE Passthrough
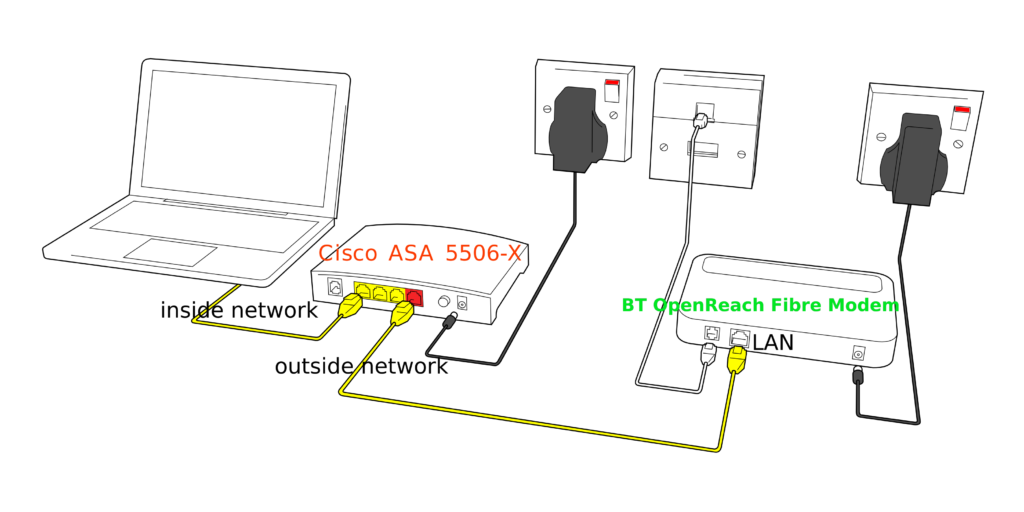
The following picture shows the Cisco ASA 5506 with a BT OpenReach Fibre FTTC Modem which perfoms the PPPoE passthrough for the Cisco ASA 5506-X. Look at the setup below;
Figure 1.0 – Cisco ASA 5506-X with BT OpenReach Fibre Modem for PPPoE Passthrough
Now let us connect our Cisco ASA 5506 to the BT OpenReach Fibre Modem or the product you have for your location. The setup will always be similar to what is in the following drawing. Select the following interfaces on your Cisco ASA 5506-X and connect them up the way it is laid out in the drawing below;
- Connect Interface X to LAN Network (In this scenario your laptop)
- Connect Interface Y to Fibre Modem (In this Scenario your BT OpenReach Fibre Modem)
- Connect DSL Line to DSL port on Fibre Modem
Figure 1.1 – How to setup Cisco ASA 5506-X for BT OpenReach Fibre Modem Passthrough
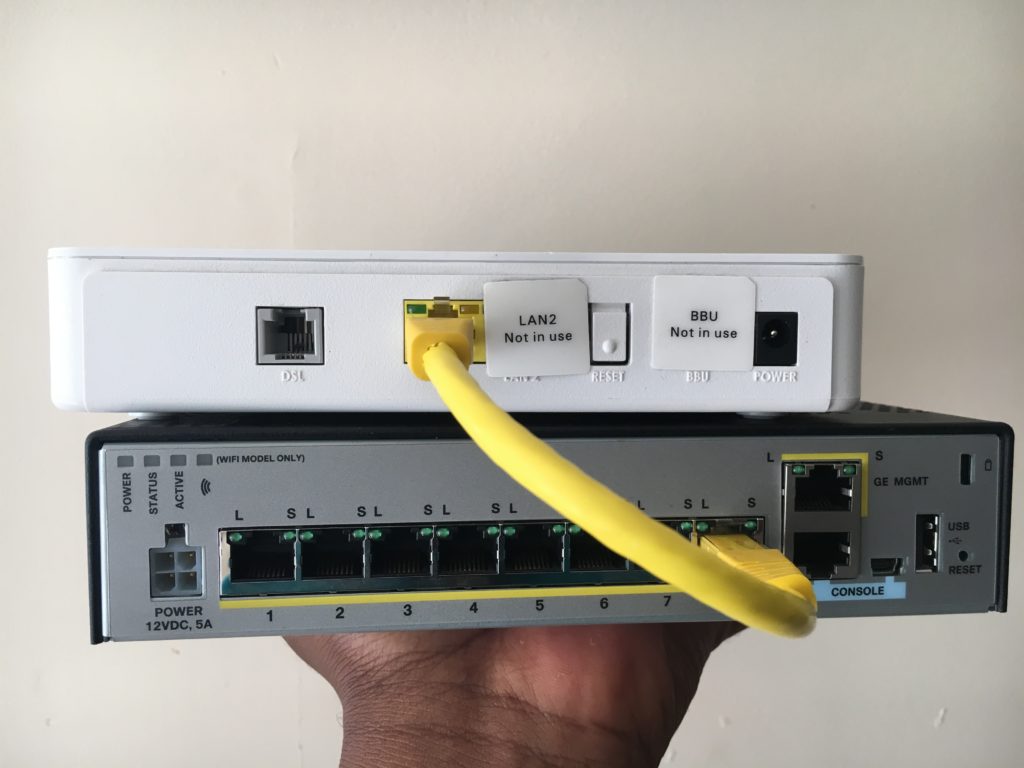
Figure 1.2 – Configure Inside Interface and Outside Interface on Cisco ASA 5506-X
I have chosen interface GigabitEthernet1/1 blue ethernet cable for my LAN Network and interface GigabitEthernet1/8 yellow ethernet cable for my Outside PPPoE Passthrough.
Follow the Instructions below to get your Cisco ASA 5506-X Up and running as PPPoE Passthrough.
Interface Configuration for Inside Network
! interface GigabitEthernet1/1 description "Inside Network LAN Interface" nameif lansubnet security-level 100 ip address 192.168.1.1 255.255.255.0 !
Interface Configuration for Outside Network over PPPoE
! interface GigabitEthernet1/8 nameif outside security-level 0 pppoe client vpdn group EE ip address pppoe setroute !
IP Scope and DNS for Connecting Clients
! dhcpd address 192.168.1.100-192.168.1.200 lansubnet dhcpd dns 8.8.8.8 8.8.4.4 interface lansubnet dhcpd enable lansubnet !
Permit Pings to test connectivity once you have completed configuring the Cisco ASA 5506-X for PPPoE Passthrough
access-list 100 extended permit icmp any any access-list from_outside extended permit icmp any any echo
Configure NAT for LAN to Reach Public Internet
! nat (lansubnet,outside) after-auto source dynamic any interface !
PPPoE Configuration – Use Chap for Fibre and PAP for ADSL
! vpdn group EE request dialout pppoe vpdn group EE localname pppoeusername.orangehome.co.uk@fs vpdn group EE ppp authentication chap | pap | mschap vpdn username pppoeusername.orangehome.co.uk@fs password ***** !
Bonus PPPoE Configuration Sample for BT Customers
vpdn group BT request dialout pppoe vpdn group BT localname bthomehub@btinternet.com vpdn group BT ppp authentication pap vpdn username bthomehub@btinternet.com password dhcpd dns 62.6.40.178 62.6.40.162 interface pppoe
Configure DNS
! dns domain-lookup outside dns server-group DefaultDNS name-server 8.8.8.8 name-server 8.8.4.4 !
SSH Configuration
!This configuration tells the firewall to expect and accept SSH from Subnet via Gig1/1 ssh 192.168.1.0 255.255.255.0 lansubnet
Verification Commands
show ip address outside pppoe show route show vpdn session pppoe state show vpdn session pppoe packets show vpdn tunnel pppoe summary show vpdn pppinterface
Results of verification commands based on debug output
ciscoasa# show ip address outside pppoe
PPPoE Assigned IP addr: 2.91.204.28 255.255.255.255 on Interface: outside
Remote IP addr: 172.16.14.167
ciscoasa# show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is 172.16.11.187 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 172.16.11.187, outside
C 192.168.1.0 255.255.255.0 is directly connected, lansubnet
L 192.168.1.1 255.255.255.255 is directly connected, lansubnet
ciscoasa# show vpdn session pppoe state
PPPoE Session Information (Total tunnels=1 sessions=1) SessID TunID Intf State Last Chg 2458 3 outside SESSION_UP 1846 secs
ciscoasa# show vpdn session pppoe packets
PPPoE Session Information (Total tunnels=1 sessions=1) LocID RemID TunID Pkts-In Pkts-Out Bytes-In Bytes-Out 2458 3 47153 37838 35440125 22334650
ciscoasa# show vpdn tunnel pppoe summary
PPPoE Tunnel Information (Total tunnels=1 sessions=1)
LocID Intf Remote MAC Sessions
3 outside 40:7c:7d:b3:79:94: 1
ciscoasa# show vpdn pppinterface
PPP virtual interface id = 1 PPP authentication protocol is CHAP Server ip address is 172.16.11.187 Our ip address is 2.31.244.218 Transmitted Pkts: 37240, Received Pkts: 47213, Error Pkts: 0 MPPE key strength is None MPPE_Encrypt_Pkts: 0, MPPE_Encrypt_Bytes: 0 MPPE_Decrypt_Pkts: 0, MPPE_Decrypt_Bytes: 0 Rcvd_Out_Of_Seq_MPPE_Pkts: 0 ciscoasa#
Cisco addresses known issues in their forum on this subject concerning Configuring Cisco ASA 550-X for PPPoE Passthrough.