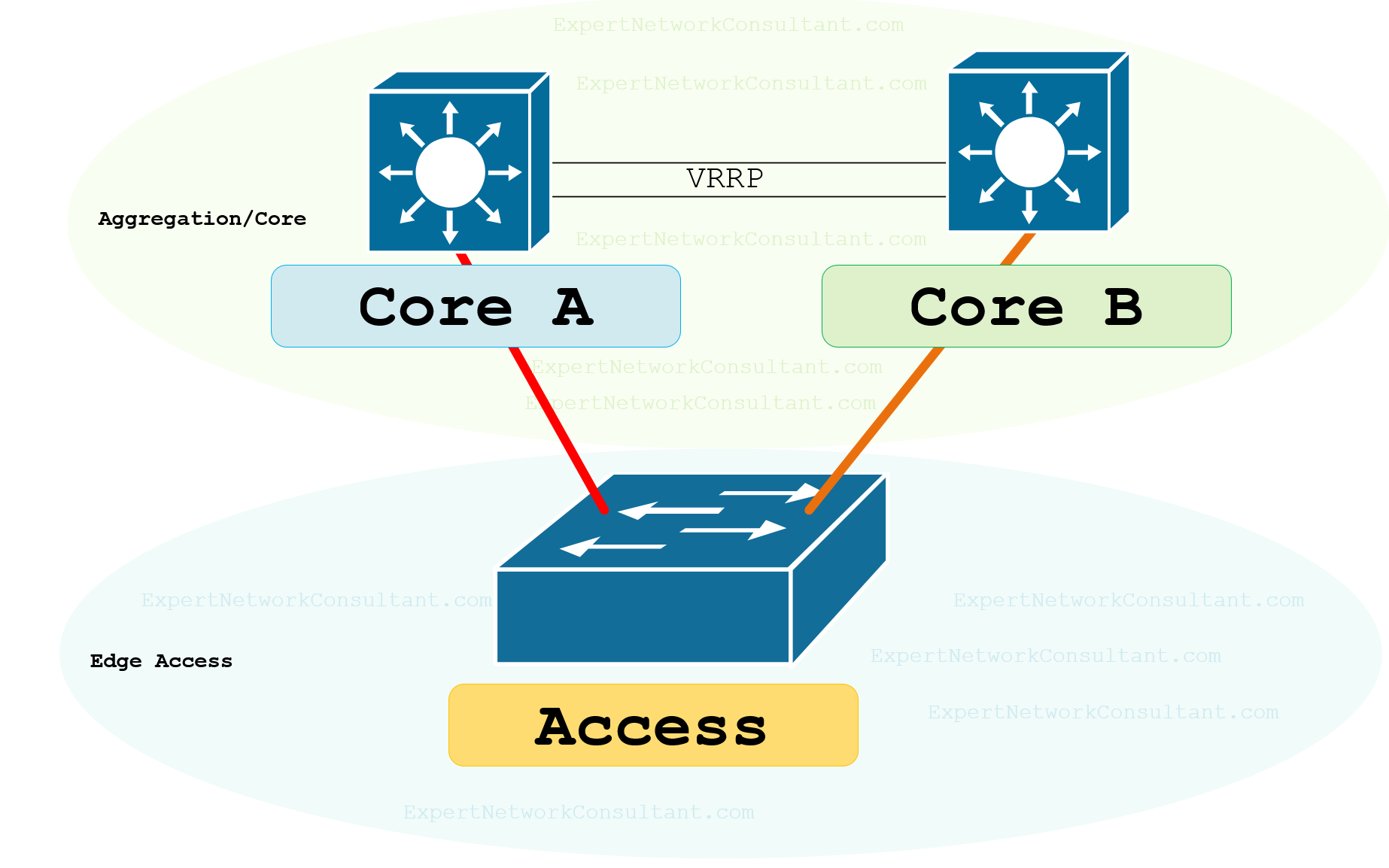
Configuring the Routed Enterprise Campus Network
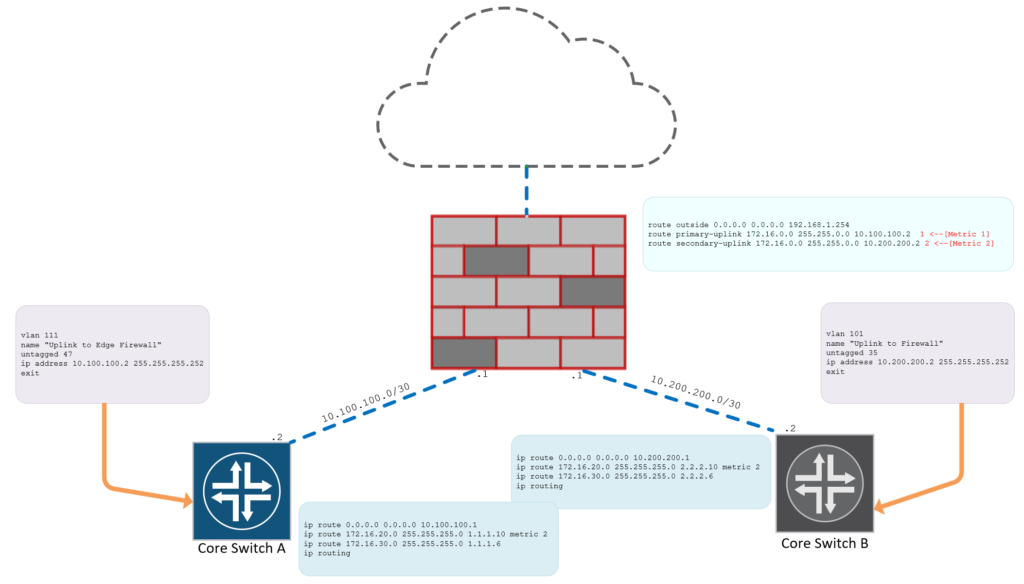
Figure 1.0 – Routed Network Design Firewall and Core Switch Configuration Setup (Click on Image to Zoom In)
Say no to something at least in your life and for us, we say no to end to end vlans focusing on configuring the routed enterprise campus network which is the enterprise network so much has been talked about. The Routed Enterprise Campus Network is the glorious loop free layer 3 routed campus design which keeps legacy layer 2 controls at bay. The likes of Spanning Tree Protocols do not have to be utilised to keep your network topology loop free. Routed networks is the answer to secured networking with much more control and segmentation abilities. Let us dive in to today’s article on Configuring the Routed Enterprise Campus Network. Let’s begin!
In this design, I have the following network devices;
The idea is to create a local vlan unique for each building with no reference of that vlan on the Core Switches allowing them to purely perform routing which keeps that core layer 3.
VLAN = Subnet = Closet
In the following configuration, I am on a Cisco Catalyst Switch and at the interface FastEthernet 1/1
How to configure a switchport as a routed port. The “no switchport” command makes the switch port converted to a routed port and that automatically enables IP Addressing. See the configuration example below;
SW1(config)# interface fastethernet 1/1 SW1(config-if)#no switchport SW1(config-if)#ip address 1.1.1.6 255.255.255.252 SW1(config-if)#no shut
If you use a HP Platform, you will not be able to convert the switchport to a routed port and so this is what you do, you create a vlan with SVI for the uplinks like the following example;
Core Switch Configuration
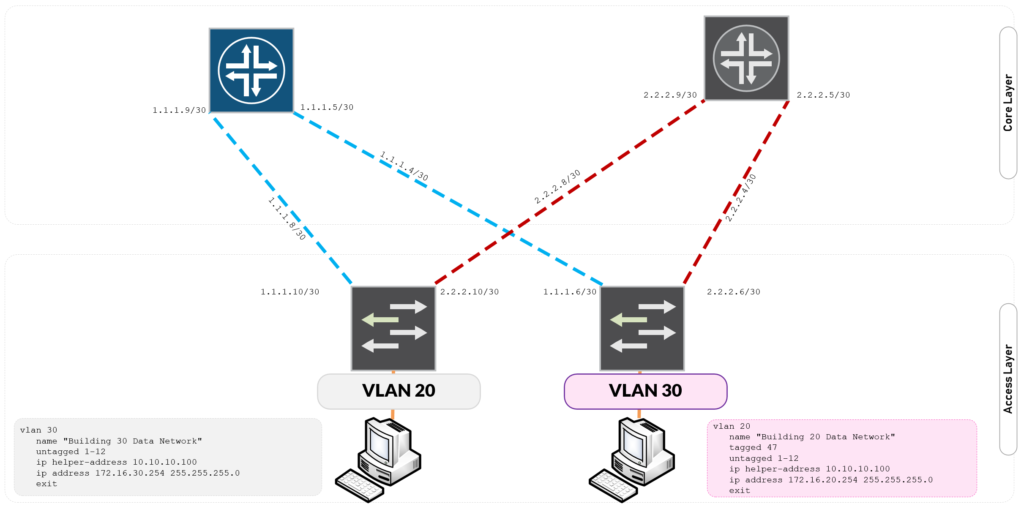
The following configuration tells the Core Switch how to reach the Building 30 Subnet which is located via the 1.1.1.8/30 subnet.
vlan 2 name "Downlink to Building 20" untagged 48 ip address 1.1.1.9 255.255.255.252 exit
Access Switch Configuration
This configuration tells the Access Switch to reach the Core Switch over the 1.1.1.8/30 subnet. Because HPE Aruba does not supported routed switchports, the interfaces participating in this interlink are placed in a dedicated vlan.
vlan 2 name "Uplink to Core Switch A" untagged 48 ip address 1.1.1.10 255.255.255.252 exit
Figure 1.1 – Routed Network Design Access Switch to Core Switch Configuration Setup (Click on Image to Zoom In)
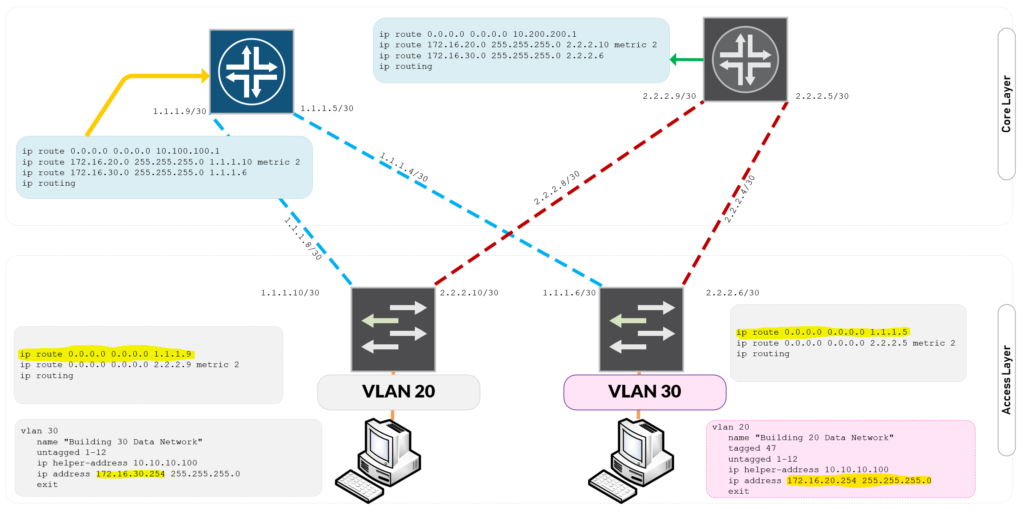
Figure 1.2 – Routed Network Design Access Switch Local VLANS to Core Switch Configuration Setup (Click on Image to Zoom In)
Join Me in this Lab as I completely configure a Routed Enterprise Campus Network
Let’s begin by configuring the firewall’s interfaces facing the following Inside and Outside security zones.
A quick breakdown of the interfaces and how they connect to their relevant uplinks
- interface GigabitEthernet1/8 – Outisde Zone (ISP)
- interface GigabitEthernet1/1 – Primary Core Switch
- interface GigabitEthernet1/2 – Secondary Core Switch
Cisco ASA 5506-X Firewall Configuration Steps
Configure interface GigabitEthernet1/8 – Outbound Uplink to ISP
! interface GigabitEthernet1/8 description "Outside Interface to BT ISP" nameif outside security-level 0 ip address 192.168.1.100 255.255.255.0 !
Configure interface GigabitEthernet1/1 – Downlink Interface to Core Switch A
! interface GigabitEthernet1/1 description "Downlink Interface to Core Switch-A Interface" nameif primary-uplink security-level 100 ip address 10.100.100.1 255.255.255.252 !
Configure interface GigabitEthernet1/2 – Downlink Interface to Core Switch B
! interface GigabitEthernet1/2 description "Downlink Interface to Core Switch-B Interface" nameif secondary-uplink security-level 100 ip address 10.200.200.1 255.255.255.252
Let’s enable SSH Access from our Private Network
crypto key generate rsa general-keys modulus 2048 username cisco password cisco aaa authentication ssh console LOCAL ssh version 2 ssh 172.0.0.0 255.0.0.0 primary-uplink
Configure Routes to the Internet and Internal Core Network Infrastructure
route outside 0.0.0.0 0.0.0.0 192.168.1.254 route primary-uplink 172.16.0.0 255.255.0.0 10.100.100.2 1 <--[Metric 1] route secondary-uplink 172.16.0.0 255.255.0.0 10.200.200.2 2 <--[Metric 2]
The above configuration lines addresses inter routing to and from the subnets behind the core switch infrastructure. Access Switch A has the Local VLAN Subnet 172.16.20.0/24 whereas Access Switch B has the Local VLAN Subnet of 172.16.30.0/24.
Remember that in a routed design, VLAN = Subnet = Closet
Network Object Group and NAT
! object network primary-uplink subnet 10.100.100.0 255.255.255.252 object network secondary-uplink subnet 10.200.200.0 255.255.255.252
Configure Network Address Translation
nat (primary-uplink,outside) after-auto source dynamic any interface nat (secondary-uplink,outside) after-auto source dynamic any interface
Core Switch A Configuration
Core-Switch-A# show vlans Status and Counters - VLAN Information Maximum VLANs to support : 256 Primary VLAN : DEFAULT_VLAN Management VLAN : VLAN ID Name | Status Voice Jumbo ------- -------------------------------- + ---------- ----- ----- 1 DEFAULT_VLAN | Port-based No No 2 Downlink to Building 20 | Port-based No No 3 Downlink to Building 30 | Port-based No No 100 Data Center Infrastructure | Port-based No No 111 Uplink to Edge Firewall for WAN | Port-based No No
Data Centre VLAN Configuration
vlan 100 name "Data Center Infrastructure" untagged 37 ip address 10.10.10.1 255.255.255.0 exit
Uplink to Firewall
Core-Switch-A# show run vlan 111 Running configuration: vlan 111 name "Uplink to Edge Firewall for WAN" untagged 47 ip address 10.100.100.2 255.255.255.252 exit
Down-links to Access Switches
vlan 2 name "Downlink to Building 20" untagged 48 ip address 1.1.1.9 255.255.255.252 exit vlan 3 name "Downlink to Building 30" untagged 46 ip address 1.1.1.5 255.255.255.252 exit
Configuring Default Routing to the Firewall
ip route 0.0.0.0 0.0.0.0 10.100.100.1
Configuring Layer 3 Routing to Local VLANS
Core-Switch-A# show run | inc ip rout ip route 172.16.20.0 255.255.255.0 1.1.1.10 metric 2 ip route 172.16.30.0 255.255.255.0 1.1.1.6 ip routing Core-Switch-A#
Core Switch B Configuration
Core-Switch-A# show vlans Status and Counters - VLAN Information Maximum VLANs to support : 256 Primary VLAN : DEFAULT_VLAN Management VLAN : VLAN ID Name | Status Voice Jumbo ------- -------------------------------- + ---------- ----- ----- 1 DEFAULT_VLAN | Port-based No No 12 Uplink to Building 20 | Port-based No No 13 Uplink to Building 30 | Port-based No No 100 Data Center Infrastructure | Port-based No No 101 Uplink to Firewall | Port-based No No 121 Interlink Connection to Switch B | Port-based No No
Uplink to Firewall
Core-Switch-A# vlan 101 name "Uplink to Firewall" untagged 35 ip address 10.200.200.2 255.255.255.252 exit
Downlinks to Access Switches
vlan 12 name "Uplink to Building 20" untagged 40 ip address 2.2.2.9 255.255.255.252 exit vlan 13 name "Uplink to Building 30" untagged 39 ip address 2.2.2.5 255.255.255.252 exit
Configuring Default Routing to the Firewall
ip route 0.0.0.0 0.0.0.0 10.200.200.1
Configuring Layer 3 Routing to Local VLANS
ip route 172.16.20.0 255.255.255.0 2.2.2.10 metric 2 ip route 172.16.30.0 255.255.255.0 2.2.2.6 ip routing
Building 20 Access Switch Configuration
Building-20(config)# show vlans Status and Counters - VLAN Information Maximum VLANs to support : 256 Primary VLAN : DEFAULT_VLAN Management VLAN : VLAN ID Name | Status Voice Jumbo ------- -------------------------------- + ---------- ----- ----- 1 DEFAULT_VLAN | Port-based No No 2 Uplink to Core Switch A | Port-based No No 12 Uplink to Core Switch B | Port-based No No 20 Building 20 Data Network | Port-based No No Building-20(config)#
Enable IP Routing and Default Route
ip route 0.0.0.0 0.0.0.0 1.1.1.9 ip route 0.0.0.0 0.0.0.0 2.2.2.9 metric 2
VLAN Infrastructure Design Configuration
vlan 2 name "Uplink to Core Switch A" untagged 48 ip address 1.1.1.10 255.255.255.252 exit vlan 12 name "Uplink to Core Switch B" untagged 40 ip address 2.2.2.10 255.255.255.252 exit vlan 20 name "Building 20 Data Network" tagged 47 untagged 1-12 ip helper-address 10.10.10.100 ip address 172.16.20.254 255.255.255.0 exit
Building 30 Access Switch Configuration
Building-30(config)# show vlans Status and Counters - VLAN Information Maximum VLANs to support : 256 Primary VLAN : DEFAULT_VLAN Management VLAN : VLAN ID Name | Status Voice Jumbo ------- -------------------------------- + ---------- ----- ----- 1 DEFAULT_VLAN | Port-based No No 3 Building 30 Uplink to Core A | Port-based No No 13 Building 30 Uplink to Core B | Port-based No No 30 Building 30 Data Network | Port-based No No
Enable IP Routing and Default Route
ip route 0.0.0.0 0.0.0.0 1.1.1.5 ip route 0.0.0.0 0.0.0.0 2.2.2.5 metric 2 ip routing
Show Local VLAN Brief
vlan 3 name "Building 30 Uplink to Core A" untagged 46 ip address 1.1.1.6 255.255.255.252 exit vlan 13 name "Building 30 Uplink to Core B" untagged 39 ip address 2.2.2.6 255.255.255.252 exit vlan 30 name "Building 30 Data Network" untagged 1-12 ip helper-address 10.10.10.100 ip address 172.16.30.254 255.255.255.0 exit
Perform Tests from Workstation
Download Full Working Configurations
See what Cisco has to say on the topic Configuring the Routed Enterprise Campus Network.
Other Related Articles:
Understanding VLANS for CCNP Switch
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server