Why Network Segmentation is Essential to Creating a Secure Enterprise Environment
In this article, Network Segmentation Best Practices to Create Secured Enterprise Environment, Senior Network Engineer, Samuel Oppong, discusses the reasons why network segmentation as a concept should be employed and implemented by enterprises in the new decade.
In The Beginning was the NAC
Network access control (NAC) was an amazing gift foundational to cyber-security efforts since the inception of networks, and it has largely remained the same for the last two decades. Organisations discovered a binary system that worked well by either allowing or denying devices access to the network. Since all devices had MAC Addresses and operated on IPV4 IP Addressing, NAC worked exceptionally well to control access to the network based on the laid down policies.
Corporate domain and guest access were in those days the only two options as the demand for innovation didn’t exist. As we have observed in recent times, there has been major changes since the revolution of internet of things (IoT).
The humongous growth and expansion in the volume of IoT devices only meant that the technology quickly posed new questions to network security that had not before been considered.
A great number of Internet of Things (IoT) and operational technology (OT) devices are not bound by the same guidelines traditional devices connected to the network follows, rendering existing NAC systems redundant and ineffective. The result of this has made companies lose visibility and control over what is connected to the network.
Then Came the Game Changer
With IT and OT devices moving away from the traditional Microsoft Windows and Linux management structure(s), NAC had had to adapt to be able to maintain high level of security. This adaptation meant NAC systems had to become agentless making it possible for its security protocol applicable to all devices across any environment. This breakthrough catapulted NAC to the next level of network security. This great advancement has been short-lived as networks have continued to grow in complexity, revealing more limitations of existing NAC models. The demand for interconnectivity across the campus, data centre, cloud and OT environments has meant that the traditional networks have outgrown the effectiveness of agentless protection and has therefore reached the threshold for innovation.
Threat actors targets large corporations and enterprises operating complex networks, such as the manufacturing industry, with increasing frequency. According to Hiscox, from 45% of businesses in 2018 to 61% in 2019 have experienced an attack. The ease at which threat actors pivot laterally across these vulnerable networks result in great disruptions and damage to both property and reputation which is critical for trust in the business circles. The Wannacry ransomware attack caused the shipping company Maersk to resort to ceasing its entire business operations and had to reinstall 4,000 servers, 45,000 computers and 2,500 applications to ensure the network was free and clear of the ransomware. This unplanned change caused severe disruption across the business and could have been averted had its network architecture limited movement once access was gained.
This has always been here – Segmentation has always been possible
Inspite of the fact that network segmentation is not a new concept, adoption across the enterprise has been very slow and, when undertaken, often tedious. This perhaps is as a result of the limitations of technologies being used in businesses such as difficulty to implement in environments outside of the data centre or blind spots such as IoT and IoT connected devices.
For an effective confrontation and onslaught of the growing combination of threats and enable zero-trust policies, network segmentation must go through an evolution to become a truly impactful approach for CISOs and IT directors in the new decade.
The initial stage or approach of this is having the full context of connected devices and applications that can be segmented across the entire enterprise from campus to data centre to cloud and OT environments. Having full visibility is the basic fundamental requirement to be able to begin segmentation and so it is paramount that you know where things are on your network. Quite simply put, if you can’t see what is there, you can’t protect it and the more granular the level of visibility is achieved, the more control you will be afforded.
Figure 1.0 -Cyber Attacks – Why Network Segmentation is Essential to Creating a Secure Enterprise Environment
Chief Information Security Officers (CISOs) at the moment encounter the real challenge of segmenting the network due to the partial context and hindered total visibility. A very handful of organisations have the ability to structure their network from the foundation and so are instead more likely to create layer network segmentation on top of the existing network. The result of such efforts only means that the underlying network is never segmented effectively and across the entire enterprise.
Although segmenting from a perspective of device context may be good, advanced network segmentation also requires traffic context. The ability to have an insight into what device(s) are communicating between each other in the existing network and what is considered legitimate traffic is paramount for Chief Information Security Officers (CISOs) today. Without the knowledge of what should be talking to what on the network, full segmentation is not possible, and you cannot guarantee that sections of the network will not break.
Figure 1.1 – Why Network Segmentation is Essential to Creating a Secure Enterprise Environment
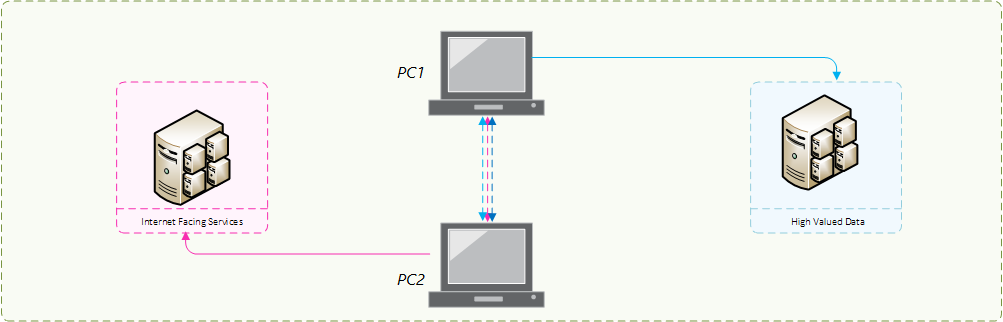
Make no mistake, without both levels of contextual information the policies are redundant. For network segmentation to be effective in today’s enterprise the enforcement of policies must be adaptable and automated, with considerations of device and traffic context that stay up-to-date with the ever-changing network.
Chief Information Security Officers (CISOs) do not have the easiest task when attempting to implement new security features across the entire network. They face challenges daily of growing number of threats while meeting more compliance directives. With the advancement of technology, the new era of network segmentation has been fashioned to allow businesses to automate the identification and isolation of threats, without impacting business operations. Many others think see data breaches as someone else’s problem assuming the position of thought ‘It won’t happen to me’…until it inevitably does. Being wise to eliminate the limiting risks, maximising control and enabling full visibility across a network, enterprises can more effectively prepare and manage the next wave of cyber threats which is currently on the rise.
Figure 1.2 – Cyber Threats – Why Network Segmentation is Essential to Creating a Secure Enterprise Environment
It is reported that the top 5 industries targeted by cyber attacks are as per below;
- Financial Services
- Services and Consultancies
- Telecom
- Manufacturing
- Insurance
Challenges facing enterprises in considering and deploying a segmented network
Lack of confidence to move forward
A great percentage of companies are in the preliminary stages of network segmentation projects, but the progress to a mature, enterprise-wide segmentation strategy is a totally different ballgame. Network architects and operations teams are currently finding it difficult to catch up with upcoming and emerging information technologies and software adoption such as the IoT, cloud, software-defined networking and digital transformation. The chosen teams may have differing agendas and are most often distributed across multiple geographies and depend on collaboration in order to get things done. Knowing of the tasks at hand and resource constraints, it is not surprising that most network segmentation projects are locked up in the early stages of planning.
Lack of skills, resources and tools
Delays to implementation, business disruptions and overly excessive operational costs all comes as a result of lack of skills and the proper toolsets. It’s no wonder organisations are struggling to plan, deploy, monitor and maintain network segmentation projects.
It is often observed that segmentation projects miss the expectations due to a lack of contextual understanding of the environment, which contributes to a collective inability to define and build the right business logic behind segmentation rules.
The well known segmentation solutions tend to be laborious, as they require manual analysis of traffic flows and logs to understand traffic dependencies. Disparate teams all too often try to build segmentation policies, mapping those policies to their siloed environments, which is likely to increase human error, inconsistent segmentation policies, and even business disruption. This approach can also result in months spent in identifying policy anomalies and validating segmentation hygiene in the environment.
Multivendor and multidomain environment complexity
Traditional segmentation is challenging enough when a network is basic, but when you factor in that most segmentation takes place in complex, multivendor, multidomain enterprise environments, implementation becomes a massive project to undertake.
In a Multivendor, Multidomain environment, employing traditional approaches such as virtual local area networks (VLANs), access control lists (ACLs), next-generation firewalls and agent overlays typically results in siloed segmentation rules that aren’t dynamic or granular enough to effectively reduce risk across campus, data center, cloud and OT environments. I hope you are beginning to appreciate this important concept?
Protecting critical business applications
• Protect business-critical applications, ensure controls are effectively enforced and continuously monitor to ensure continuous protection. Maintain appropriate intra- and inter business service controls across different services, applications and domains.
• Control user access to critical business services across different domains. Protect business critical applications from misuse by users, ensure controls are effectively enforced and continuously monitor ongoing protection.
Enforce privileged access to critical IT infrastructure
Restrict IT admin access to sensitive network devices (switch, NGFW, etc.) and data center/cloud workloads (Active Directory/LDAP, Domain Name System, Oracle Cluster, etc.) based on designated admins (role-based), IT admin endpoint state (encrypted, domain-joined, etc.) and secure communication (specific port/service)
Protecting enterprise IoT/OT devices (printers, cameras, VoIP, card reader, HVAC, etc.)
Protect the IT network from IoT/OT devices – as discussed in earlier paragraphs, it is best to keep IoT’s in their dedicated segment.
• Protect IoT/OT devices from attacks
Enterprise-wide segmentation assurance
Ensure all enforcement points across different domains (campus, data center and IoT), managed by other teams, are meeting segmentation policy requirements and configured as intended.
Containment of vulnerable devices
Limit access from/to vulnerable devices (WannaCry, unpatched, end of life, etc.) to the rest of the network.
Protecting legacy applications/OS devices
Reduce the attack surface by segregating devices with legacy operating systems and applications installed on them
• Mitigate risk of threats to devices running end-of-life operating systems
Why modern enterprises need network segmentation
As businesses become more digital and connected, and cyber attacks become more sophisticated and destructive, it is becoming increasingly clear that enterprises need a new approach to security.
Welcome to Network Segmentation
Network segmentation is arguably one of the most powerful but underestimated security steps and a cornerstone of a successful information security program. This concept when implemented directly addresses the realities of today’s threat landscape—that you cannot prevent a cyber breach, but you can isolate one. Segmentation makes it possible to isolate or quarantine a breached zone without crippling your entire enterprise network.
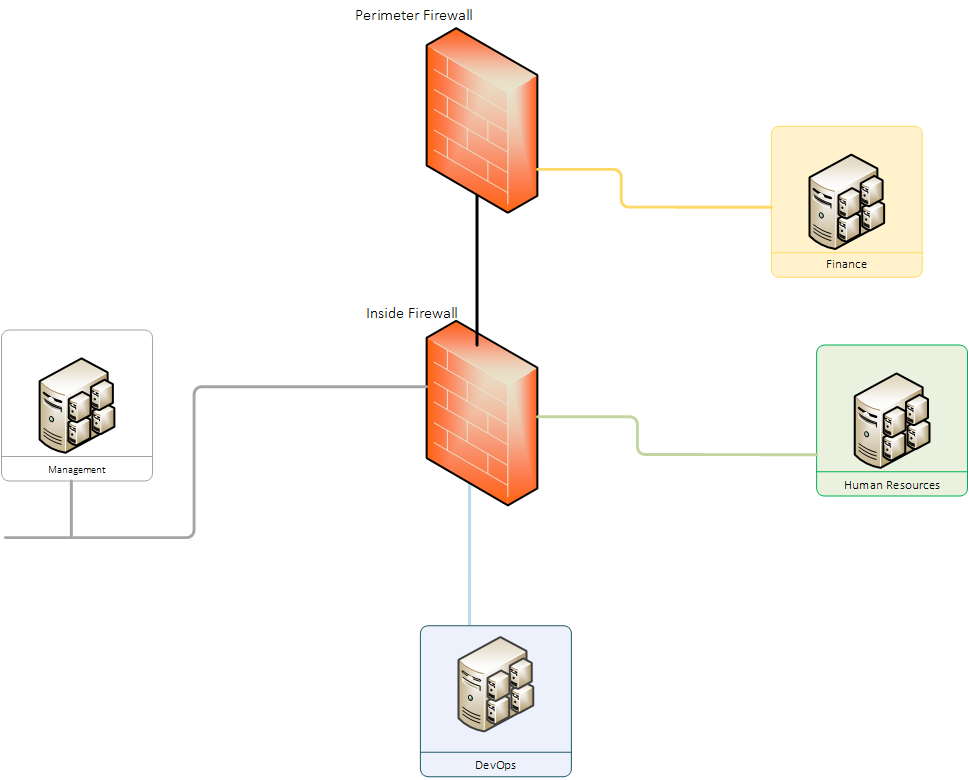
The focus of Network segmentation is in separating parts of the network from one another with barriers or controls.
It makes applying policies to segmented zones much easier and effective. Imagine the ability to monitor all traffic coming in and out of the Human Resources Department and applying the appropriate policies so you are able to create baselines based on expected behaviours? Where the segmentation effort covers function — for example, the DevOps system is segmented from the HR system, this also makes it possible to apply policies or rules to the functions. In another approach, the segmentation occurs by data classification — for example, sensitive or regulated data, such as personally identifiable information (PII), is isolated from the rest of the network.
By implementing network segmentation, modern enterprises can help address today’s major cyber security challenges far better than with flat networks. When a proper network segmentation is implemented, it lays down the groundwork for controls which defends and protects against (East-West) lateral movement on the network by ill intending malicious software and actors, preventing a potential infection or compromise from spreading across the entire network. This allows for additional control points across the network, making significant increase in visibility and control over traffic on the network.
Since the vast majority of breaches are thought to occur toward the network periphery, it is clear that proper network segmentation should be the starting point for protecting modern enterprises.
Flat Networks – Flat networks focus on providing reliable and fast connectivity for all devices on the network, meaning all devices have equal access to the network and all services and information that reside on it.
In fact, one of the most infamous corporate data breaches to date—the massive hack of a major retailer in 2015—was partially blamed on improper network segmentation. According to Computerworld, hackers broke into the retailer’s network using login credentials stolen from a third-party contractor. They then leveraged that access to move through the network, eventually accessing the company’s point-of-sale systems (POS), which handled sensitive consumer payment card data.
A framework for implementing network segmentation
I have read through KPMG’s framework document and pleased with the laid down recommendations. View resource | A framework for implementing network segmentation.
According to research commissioned by Avaya, although virtually all information technology professionals believe network segmentation is an essential security measure, less than one-quarter of organisations actually implement it. The biggest stumbling block? Complexity.
There is no getting around it: Implementing network segmentation is a vital but incredibly significant organisational effort. Businesses may need to add or replace hardware and software. They may need to integrate existing solutions in different and new ways. The people who manage the network may need to change, as may the processes governing the network. Even the users of the network may need to transform.
Below, describes 10 components of trusted framework for network segmentation.
Businesses challenged to phase out outdated network infrastructure and update their network to handle the security challenges of today and tomorrow can use this framework as a basic guide to getting started on network segmentation.
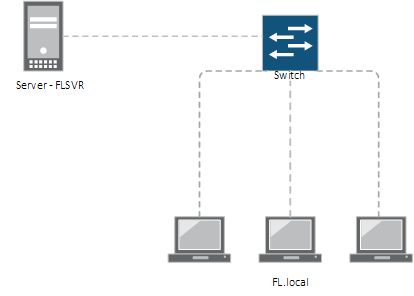
Figure 1.2 – Network Segmentation Framework – Why Network Segmentation is Essential to Creating a Secure Enterprise Environment
Strategy
The plan of action
Creating a network segmentation strategy is essentially the guiding document for the overall network segmentation effort. This strategy helps to document the organisation’s goals and defines the parameters for the segmentation. A tier of segmentation could be initiated from the regional level that is creating subnetworks based on the geographical location of the business and afterwards moving down to the functional level where the divisions of departments or functions like HR Systems from Finance Systems). The last bit would be to and finally segment at the data level that is ensuring that sensitive data types like intellectual property are well protected in secured zones segmented well away from other zones.
Network architecture
The blueprint
To build things right, it’s best to have a design or an idea on paper what you want to see. The network architecture foundational to network segmentation or the implementation blueprint of the network segmentation strategy. This design or architecture shows the number of segments and the number and type of control points between segments, see Figure 1.2.
IT asset management
Defining who is on the network
To thoroughly validate and authorise devices for the network, a comprehensive IT asset management programme must be instituted. With the implementation of IT asset management, the network segmentation effort helps to define the requirements for segmentation and network authorisation levels based on the user, device and location.
Network access control, firewalls and intrusion prevention systems
The core security controls
A good number of technology solutions works hand in hand to prevent malicious actors and malware from entering and moving through the segmented network. Intrusion prevention systems monitors and detects the presence of bad actors on the network. Routers and firewalls direct the flow of traffic between segments based on user and device criteria. Finally, network access control limits admission to the network based on compliance to the organisation’s security policies. For example, it validates that only authorised users and devices—those which meet the network segment’s security requirements—are allowed on that particular network segment.
Behavior-based protections
Dynamic, next-generation security controls
The ability to leverage advanced user analytics, makes organisations able to make behavioral analysis a next-level control on the network. This enables more sophistication in how the network prevents, detects and responds to cyber threats. With user analytics, the organisation is able to map out a baseline profile of each user —i.e., who they are, what device they use, where they connect from, and how they authenticate their identity. Once the profile is in place, the network can spot deviations from normal user behavior—even if it is within the allowed traffic—and dynamically adjust how they treat that user based on that change in behavior. For example, if a user who normally never transmits any data externally suddenly starts transmitting large amounts, it may be a valid action—or it may indicate a breach, malware infection or insider threat. Having detected this change in behavior, the network would automatically quarantine the potentially compromised user to allow for further investigation, prevent a possible breach in progress, and expedite any required remediation effort.
Network policy management tools
Automating security rule improvement
Network policy management tools continuously analyze the traffic on the network and compare it to the control rules. Based onoutcome of these analysis, the tools inteliigently suggest improvements to the rules to provide a more granular filtering. This empowers the ability to migrate to a strategically segmented network by initially leveraging a relatively open rule base and then automatically defining more granular rules based on traffic flows – flows determined from careful observation and analysis.
Data center micro segmentation
Protecting the highest-priority systems
The security of data centers, which house the network’s most critical systems, is a top priority for organisations. As common practice, data centers are one segment of the larger network, fenced securely by perimeter security technologies. Only authorised devices are permitted to access the data center and resources tied to that segment. Interestingly, inventive cyber actors have now demonstrated the ability to compromise even authorised devices which was not possible in the past. Once they gain entry, they can often wreak havoc across the data center. Micro segmentation is one great way helping in recent times to prevent the spread of intrusions by dividing the data center into even smaller zones, enabling organisations to stop intruders from moving freely about the data center segment, sandboxing for lack of a better term breaches within the most crucial enterprise systems hence preventing an explosion of sudden attacks or infections due to the breach.
Data classification
Enabling data center micro segmentation
Network segmentation based on data classification, a common approach in the data center, requires a comprehensive data classification program. With the data classification program, it is possible to not only define micro segments, but also define different authorization levels based on the user, device, location and data being accessed.
Keeping Everything on Track
A dedicated programme management and an architecture management are critical pieces of a network segmentation project, in place to keep the project on track from the get-start-go. These functions provide directives and leading over network architecture decisions throughout the course of the project. This dedicated programme management, provide quality assurance, maintain schedule, budget and resources, and provide status reporting for stakeholders.
Organisational Change Management
Getting the organisation aligned
Implementing network segmentation is really about transforming the network from a flat network to a modern and secure network. As with any technology transformation, the people and processes connected to the network have to transform, too. These changes should be handled through an organisational change management function, which drives the changes throughout the organisation. This function helps ensure end users are informed, engaged and able to make the required behavioral changes. It also develops strategies, plans and tactics to obtain key stakeholder buy-in, communicate effectively, mitigate stakeholder resistance, and train and educate impacted people.
Final Thoughts
If your organisation has not implemented network segmentation, now is the time to consider it. Just as the smart king would never depend on a single gate to secure his kingdom, a smart business leader would never rely on a single control point to protect the organisation’s assets.
Network segmentation—which limits the damage of a breach—is arguably the leading defense against the latest, sophisticated security threats. As corporate hacks become more frequent and devastating, impacting large and small businesses in every industry, network segmentation has become an imperative for the modern enterprise. Effective network segmentation is a huge undertaking. But if you break it down to its basic pieces—the 10 components as in the above framework—it becomes significantly more manageable to implement proper network segmentation to better protect your enterprise.
Other Good Reads:
Configuring the Routed Enterprise Campus Network
Network Segmentation How To Tips
Creating a Secured Azure Network Framework
