Remote Desktop Connection does not always work with Cloud Machines. If you want to know How to Successfully RDP into Azure AD-Joined Virtual Machines, then this article is all you’d ever need.
If you have struggled to remote desktop to a virtual machine in Azure, then it is likely to be a Windows Server or Desktop machine.
Azure uses the AzureAADLogin extension to enable the capabilities of user logins with their domain credentials.
It doesn’t always work and in my experience, I haven’t had much success with it up until now when I have finally figured out how to successfully rdp into a azure ad-joined vm in Azure.
Below are the steps needed to successfully achieve our objective.
Step 1: Create a Virtual Machine
az group create --name your-resourcegroup-name --location westus
az vm create \
--resource-group your-resourcegroup-name \
--name your-vm-name \
--image Win2019Datacenter \
--assign-identity \
--admin-username localadminuser \
--admin-password yourpassword
Although this extension can be installed at the time of creation of the virtual machine, using the following bash commandlet would still install the extension for you.
Step 2: Install Required Extensions
az vm extension set \
--publisher Microsoft.Azure.ActiveDirectory \
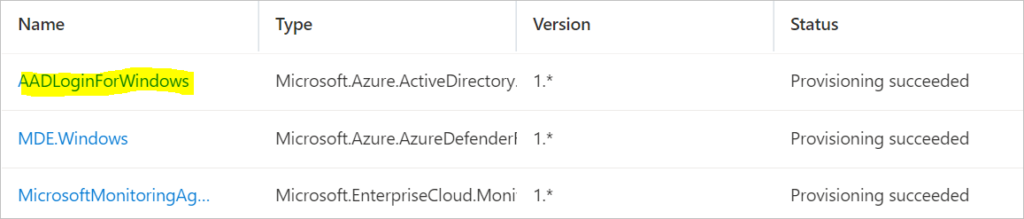
--name AADLoginForWindows \
--resource-group your-resourcegroup-name \
--vm-name your-vm-name
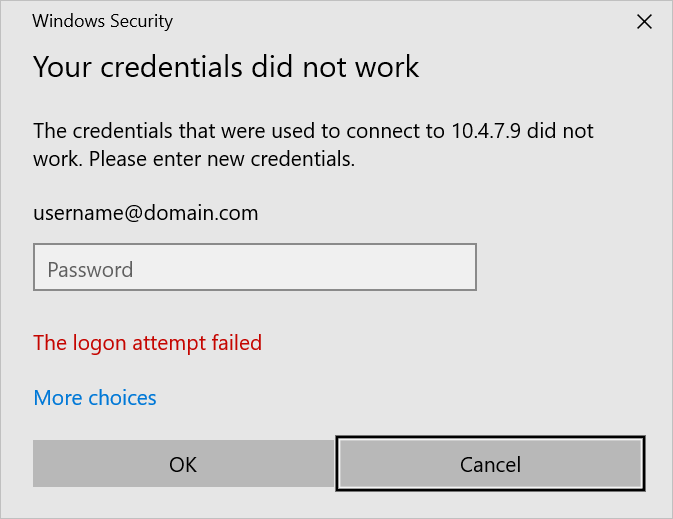
This article is intended to fix a peculiar problem encountered in remote desktop connections to Windows Server Virtual Machines on Azure. With the local administrator account, I could remote desktop to the virtual machine but not with domain accounts.
Figure 1.0 – The Logon Attempt Failed.
Install required extensions for the virtual machine
Install WindowsAADLogin Extension with RBAC
Enable Remote Desktop Access | 3389 on the NSG
This can be done at the creation of the virtual machine.
Now that you’ve created the VM and enabled the appropriate extension(s), you need to configure an Azure RBAC policy to determine who can log in to the VM. Two Azure roles are used to authorize VM login.
Add either of these IAM Roles to RBAC User
Users who have this role assigned can log in to an Azure virtual machine with regular user privileges.
Users who have this role assigned can log in to an Azure virtual machine with administrator privileges.
$username=$(az account show --query user.name --output tsv)
$rg=$(az group show --resource-group your-resourcegroup-name --query id -o tsv)
az role assignment create \
--role "Virtual Machine Administrator Login" \
--assignee $username \
--scope $rg
Mitigation | Steps I followed to fix this issue.
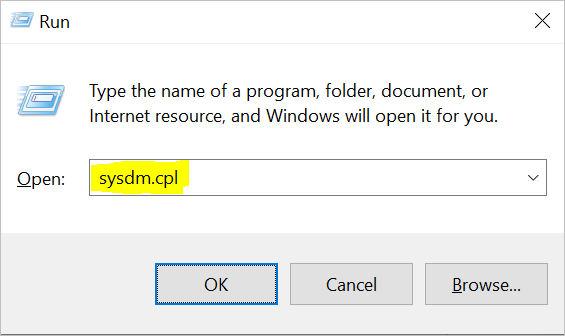
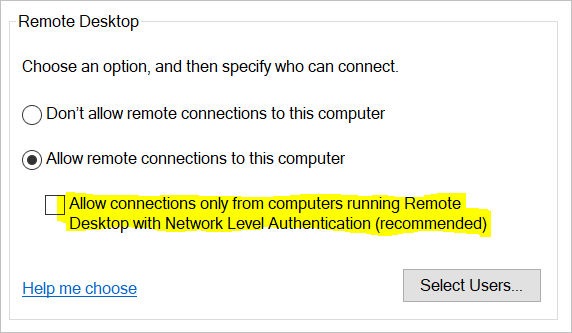
Windows Key + R
Type sysdm.cpl a
Uncheck the Allow connections only from computers running Remote Desktop with Network Level Authentication (recommended) box.
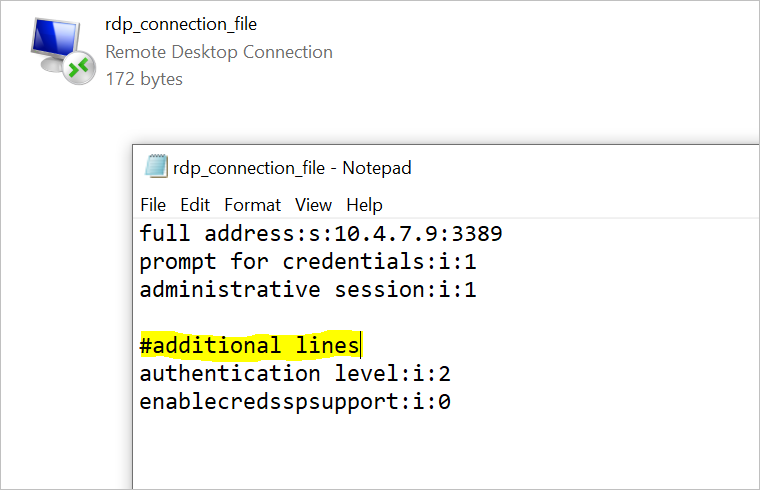
Edit the RDP file
Add the following lines to the RDP Connection file with a text editor of your choosing. Save the file ensuring its not formatted as any other file type except with the extension *.rdp
authentication level:i:2
enablecredsspsupport:i:0
Add a space character before the AzureAD domain.
#optional line – make a note of the full-stop character before the \azuread\
full address:s:10.X.Y.Z:3389 prompt for credentials:i:1 administrative session:i:1 authentication level:i:2 enablecredsspsupport:i:0
username:s:.\azuread\username@domain.com.\azuread\username@domain.ext
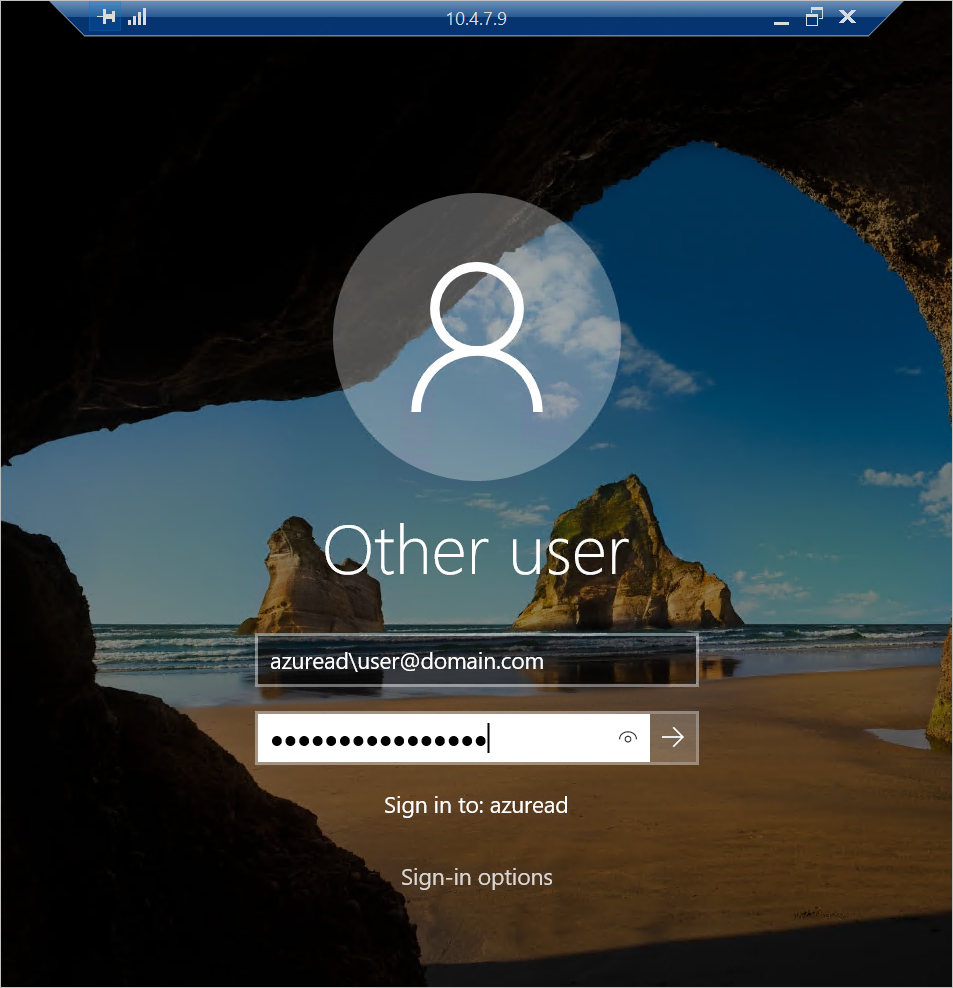
If you are not interested in the optional line configuration, then you will now need to enter your credentials once connection is initiated as thus;
username: azuread\user@domain.com password: **************
make a note of the space character before the AzureAD domain
Initiate Connection to Virtual Machine
If you have followed the above steps diligently, then the attempt to login failure should no longer exist.
Below is a helpful community article addressing this challenge.
If you want to learn more of how to troubleshoot virtual machines, then please follow this useful resource from Microsoft.