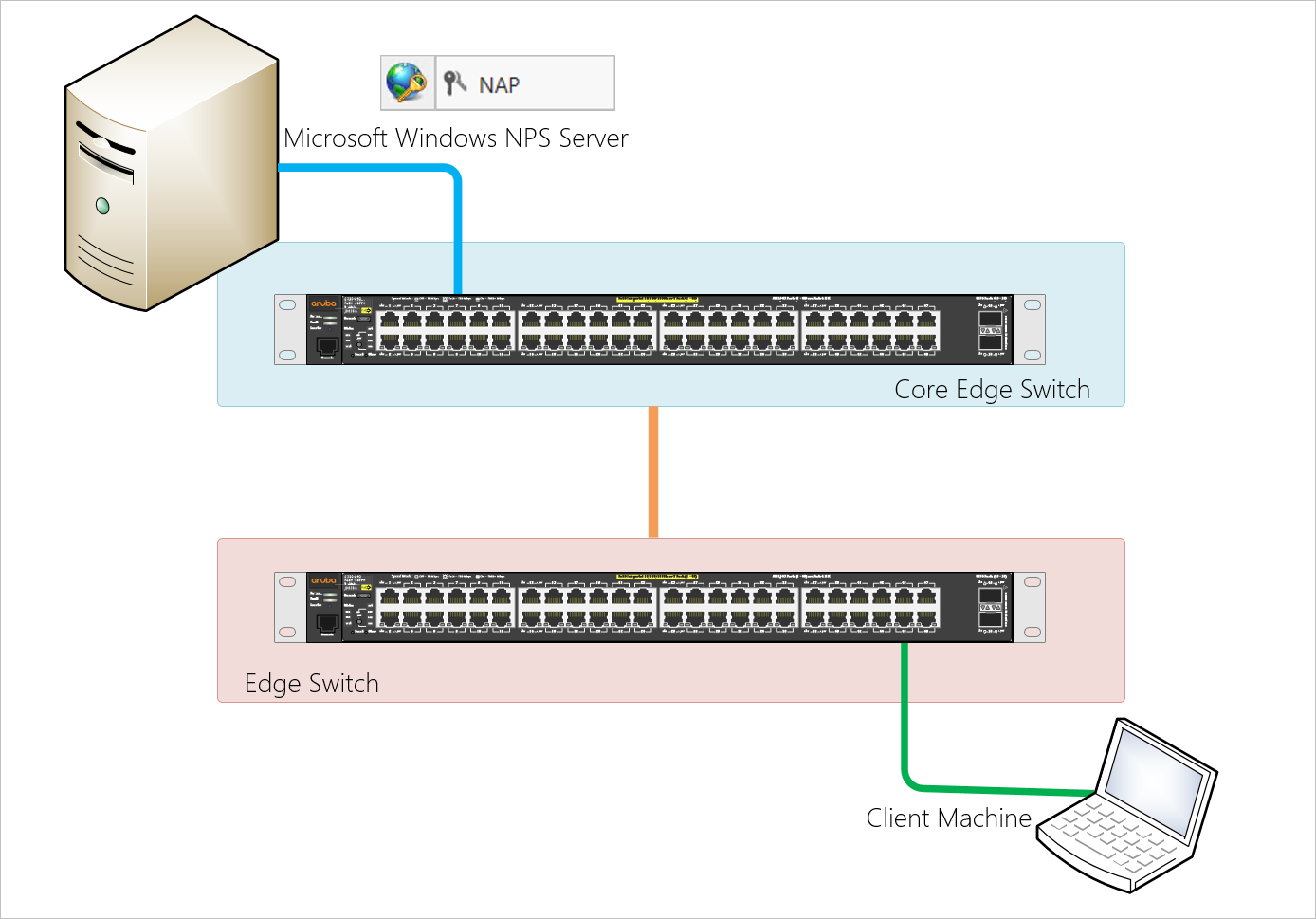
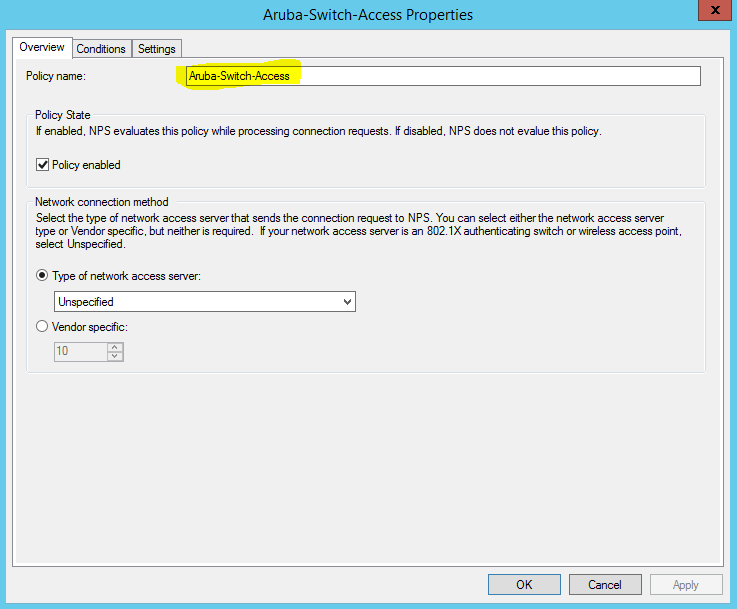
How do you configure Network Device Management with RADIUS Authentication using Windows NPS to authenticate management SSH connections to Network Devices?
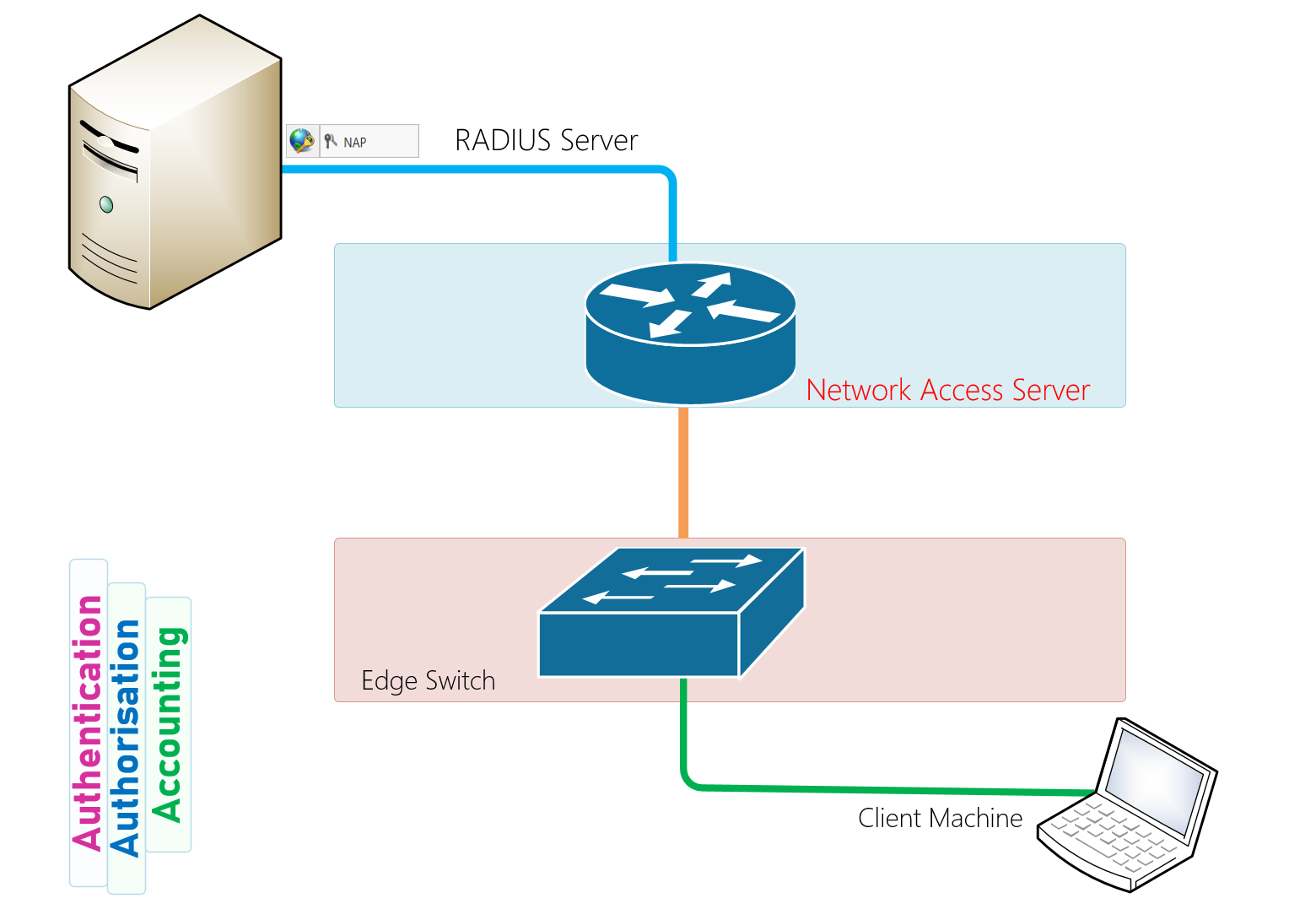
Technologies Used In Our Scenario today to deploy Network Device Management with RADIUS Authentication using Windows NPS are the following;
Network Equipment
- HP Aruba 2920
- Cisco Catalyst 2960
- Cisco ASA 5505 Firewall
You have heard many say AAA is the best security model for user access and management to network devices. Well, it is and as a good professional practice, securing network devices using the Triple A process meets many best security practices of our day.
Authentication
Authentication is the first process which provides a way of identifying a user ho requires access to network resource, typically by having the user enter a valid user name and password before access is granted. The process of authentication relies on each user requiring access to having a unique set of criteria for gaining the appropriate access desired. The AAA server which in our case is the Microsoft Network Policy Server compares a user’s authentication credentials with the user credentials stored in a database which in our case is the Windows Active Directory. If the credentials match, the user is granted access to the network. If the credentials are at variance, authentication fails and network access is denied.
Authorisation
Now that the user has been successfully authenticated, a user must gain authorisation for doing certain tasks. After logging into a network device for instance, the user may try to issue commands. The authorisation process determines whether the user has the authority to issue such commands. Authorisation simply is the process of enforcing policies: determining what types or qualities of activities, resources, or services a user is permitted. Usually, authorisation occurs within the context of authentication. Once you have authenticated a user, they may be authorised for different types of access or activity.
Accounting
The final plank in the AAA framework is accounting, which measures the resources a user consumes during access. This can include the amount of system time or the amount of data a user has sent and/or received during a session. Accounting is carried out by logging of session statistics and usage information and is used for authorization control, billing, trend analysis, resource utilization, and capacity planning activities.
Authentication, authorisation, and accounting services are often provided by a dedicated AAA server, a program that performs these functions. A current standard by which network access servers interface with the AAA server is the Remote Authentication Dial-In User Service (RADIUS) which we have used the Microsoft NS server for in our deployment.
Network Device Management with RADIUS Authentication using Windows NPS Step by Step Guide.
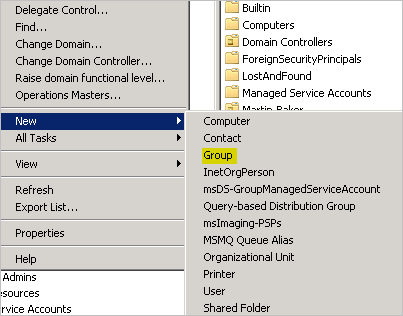
Step 1: Configure Active Directory Infrastructure
Specify Name for Security Group
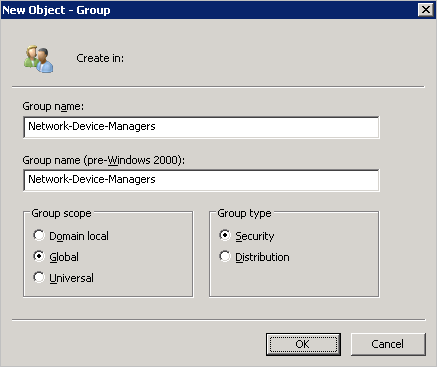
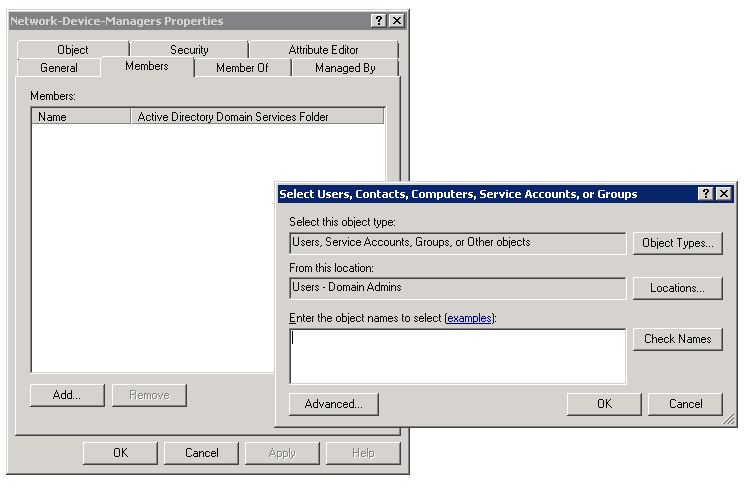
Add Network Administrators to Group Created
Configure NPS Server : IEEE 802.1X Authentication and Dynamic VLAN Assignment
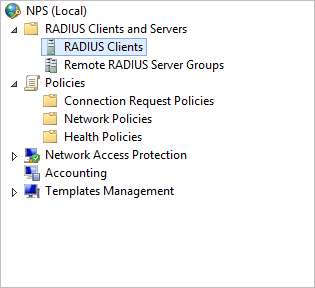
Step 2: Configure RADIUS Infrastructure
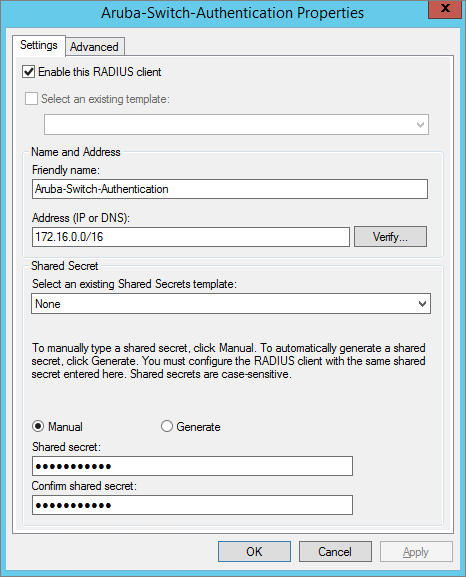
Create RADIUS Client
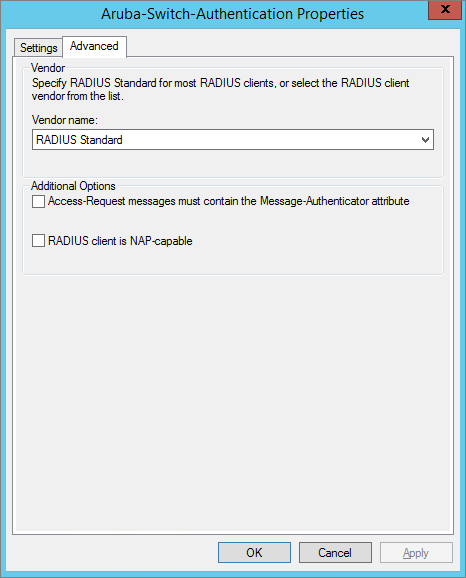
Create RADIUS Client and Enable RADIUS Standard
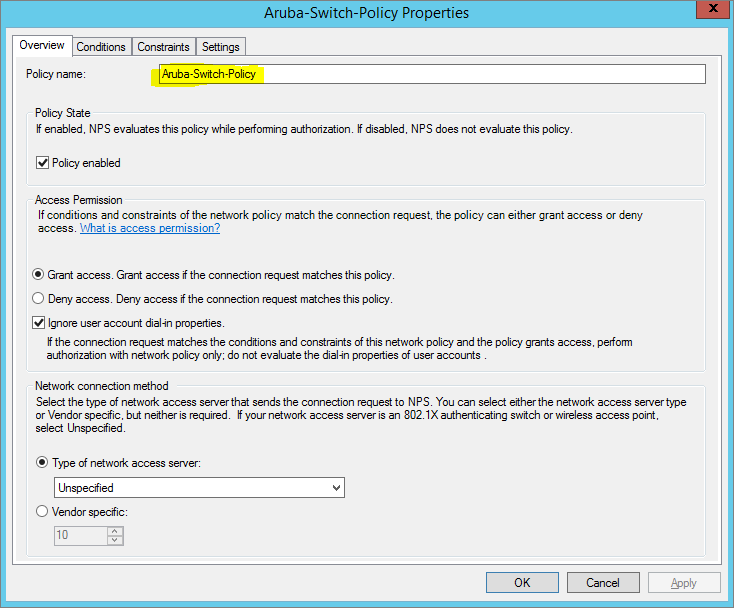
Create Network Policy
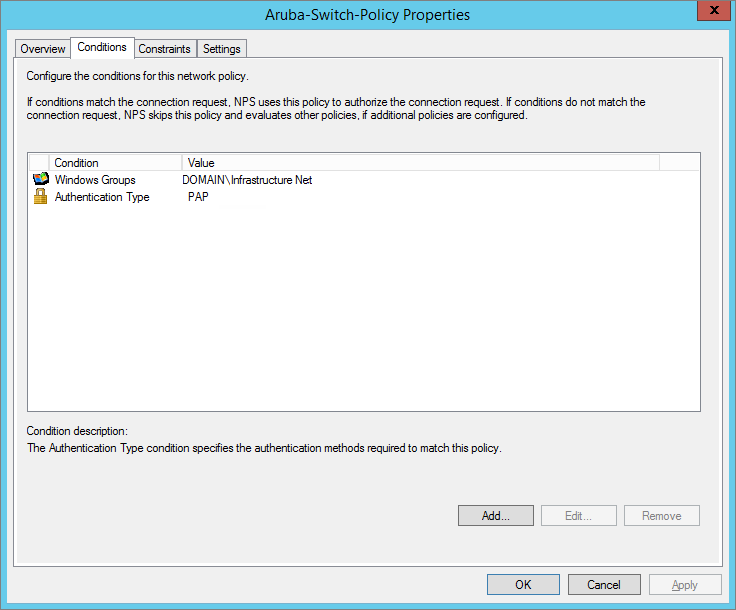
Create Policy – Conditions
Then, in the Network Policies section create a new authentication policy. Enter its name, e.g., Network Switch Auth Policy for Network Admins. Create two conditions: in the first one, Windows Groups, specify the domain group, which members can get authentication (the accounts of the network administrators are in the AD Network Admins group in our example). The second condition, Authentication Type, is to select PAP as the authentication protocol.
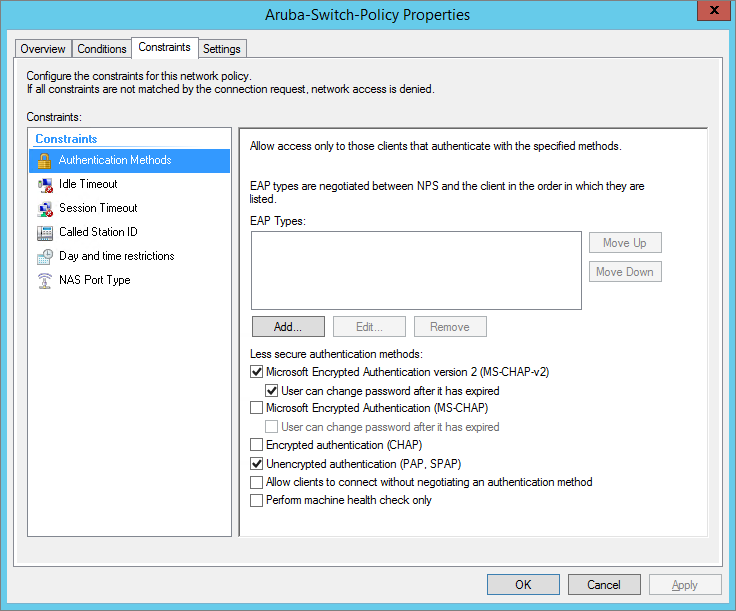
Then in the Configure Authentication Methods window, uncheck all authentication types, but for Unencrypted authentication (PAP. SPAP).
Create Policy Constraints – Authentication Methods
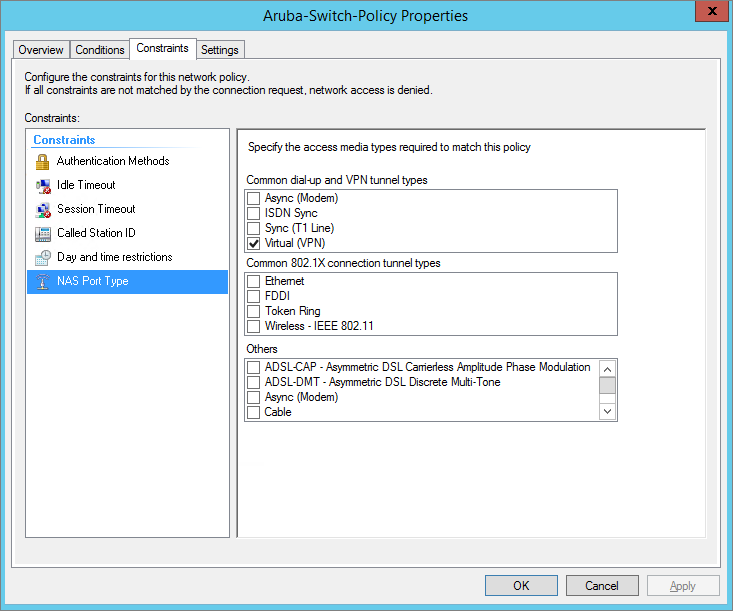
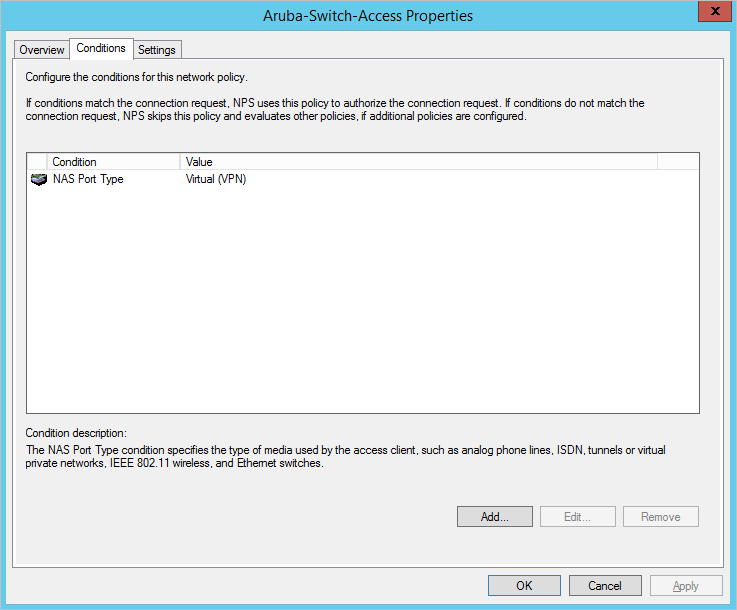
Create Policy Constraints – NAS Port Type Virtual(VPN)
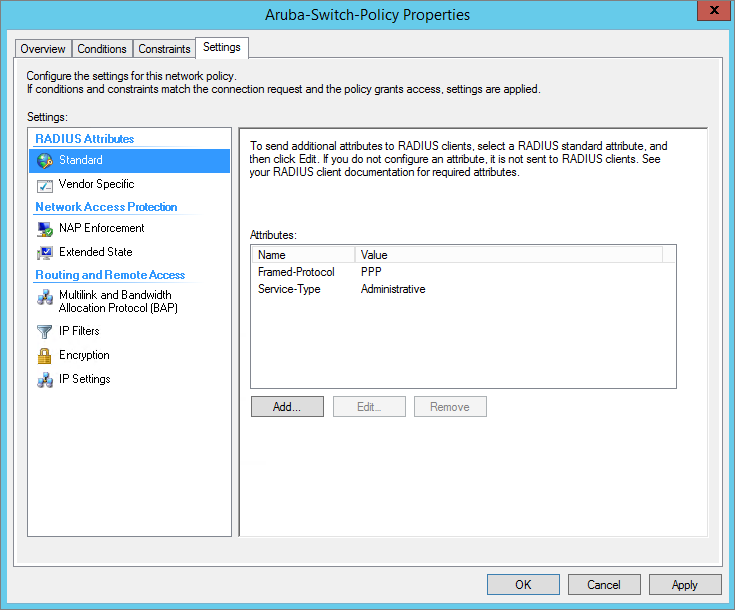
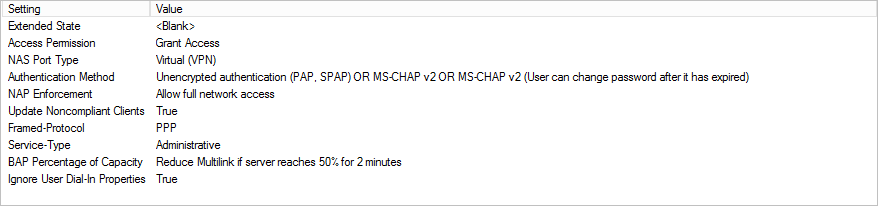
Create Policy Settings – Standard Attributes
Framed-Protocol: PPP
Service-Type: Administrative
In the Configure Settings window, change the value of the Service-Type attribute to Administrative.
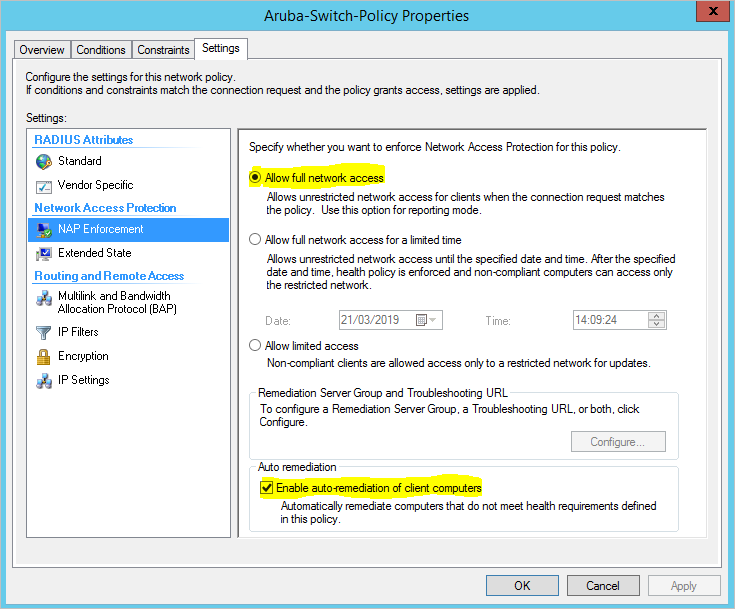
Network Policy – NAP Enforcement and Auto Remediation
Network Policy Condition
Condition Value
------------ ---------------------
Windows Groups: Domain\Security Group
Authentication Type: PAP
Network Policy Settings
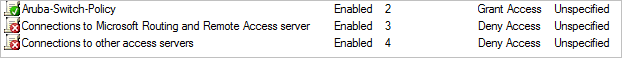
Create Connection Request Policy
Connection Request Policy Conditions NAS Port Type Virtual VPN
Step 3: Configure Network Devices for RADIUS Authentication
For Cisco Devices – Create a Network Policy like the above but additionally include the following setting.
Under Vendor Specific we need to add to a Cisco-AV Pair to tell the router to go to privilege level 15, select next when you add the “shell:priv-lvl=15” in the Cisco-AV.
shell:priv-lvl=15
Configuring AAA on Cisco IOS
aaa new-model radius-server host 172.16.4.192 auth-port 1645 acct-port 1646 key YOUR_SECRET_KEY aaa authentication login default group radius local aaa authorization exec default group radius local ip radius source-interface Vlan124 line con 0 line vty 0 4 line vty 5 15
Configuring AAA for Cisco ASA
aaa-server RADIUS protocol radius aaa-server RADIUS host 172.16.4.192 key YOUR_SECRET_KEY radius-common-pw YOUR_SECRET_KEY aaa authentication telnet console RADIUS LOCAL aaa authentication ssh console RADIUS LOCAL aaa authentication http console RADIUS LOCAL aaa authentication http console RADIUS LOCAL
Configuring AAA on HP Aruba 2920 Switch
Enable and Specify RADIUS Authentication Server
radius-server host 172.16.4.192 key "YOUR_SECRET_KEY" acct-port 1646 auth-port 1645 radius-server retransmit 2
Enable SSH Login via RADIUS
aaa authentication ssh login radius local aaa authentication ssh enable radius local
Enable Web Login via RADIUS
aaa authentication web login radius aaa authentication web enable radius aaa authentication web-based peap-mschapv2
Enable Authentication and Accounting Parameters
aaa accounting commands interim-update radius aaa authentication num-attempts 7 aaa authentication login privilege-mode
PS: The following command is what will get everything working for you as without it; you will get the error below;
Access denied: no user’s authorization info supplied by the RADIUS server
![]()
Golden Command to allow SSH Sessions to Switch
aaa authorization commands none
Verify and Troubleshoot
Check Switch RADIUS Authentication
Aruba-Edge-Switch# show radius authentication
Status and Counters - RADIUS Authentication Information
NAS Identifier : Aruba-Edge-Switch
Invalid Server Addresses : 0
UDP
Server IP Addr Port Timeouts Requests Challenges Accepts Rejects
--------------- ----- ---------- ---------- ---------- ---------- ----------
172.16.4.192 1645 0 66 0 47 19
Check Recent SSH Logins
Aruba-Edge-Switch# show authentication last-login Username Priv Last Login Last Login IP Address --------------------------------------- ----- ------------------- --------------------------------------- ----- ------------------- esmith Mgr 2019-03-21 13:18:28 172.16.122.120 jarif Mgr 2019-03-21 09:56:57 172.16.122.196 rjenson Mgr 2019-03-21 13:52:40 172.16.122.109 dplomar Mgr 2019-03-21 10:51:28 172.16.122.109
On Microsoft NPS Server 2012 R2 – Launch Events Viewer
Check Authentication Informational Log Reporting
Check Event Logs
Network Policy Server granted access to a user. User: Security ID: MercuryLabs\soppong Account Name: soppong Account Domain: MercuryLabs Fully Qualified Account Name: MercuryLabs\soppong Client Machine: Security ID: NULL SID Account Name: - Fully Qualified Account Name: - OS-Version: - Called Station Identifier: - Calling Station Identifier: 172.16.122.109 NAS: NAS IPv4 Address: 172.16.122.19 NAS IPv6 Address: - NAS Identifier: Aruba-Edge-Switch NAS Port-Type: Virtual NAS Port: - RADIUS Client: Client Friendly Name: Aruba-Switch-Auth-Corp Client IP Address: 172.16.122.19 Authentication Details: Connection Request Policy Name: Aruba-Switch-Access Network Policy Name: Aruba-Switch-Corp-Policy Authentication Provider: Windows Authentication Server: NPS-Server.expertnetworkconsultant.com Authentication Type: PAP EAP Type: - Account Session Identifier: - Logging Results: Accounting information was written to the local log file. Quarantine Information: Result: Full Access Session Identifier: -
I hope you have enjoyed this article on Network Device Management with RADIUS Authentication using Windows NPS.
Follow the following links for further understanding of the topic: